- by Dave Gunter
- Thursday, October 11, 2018
- Industrial Cybersecurity
Managing Unconfirmed Cybersecurity Vulnerabilities like Supermicro
Unconfirmed vulnerabilities are not usually a big issue, but when one occurs like Supermicro, plant management will ask a simple question: “Do we have an issue or not?”
Having been on the receiving end of this blunt exchange, I realize it can be painful and embarrassing to communicate,…
Read More...
- by Hal Thomas, CFSE
- Thursday, August 25, 2011
- Functional Safety
PHA to LOPA: Part I
Parts I and II of this article provide a framework for when it is appropriate to make the transition from qualitative analysis to more quantitative during the hazard review work process. It further illustrates that LOPA can be used as part of what is considered more qualitative analysis…
Read More...
- by Hal Thomas, CFSE
- Tuesday, August 30, 2011
- Functional Safety
PHA to LOPA: Part II
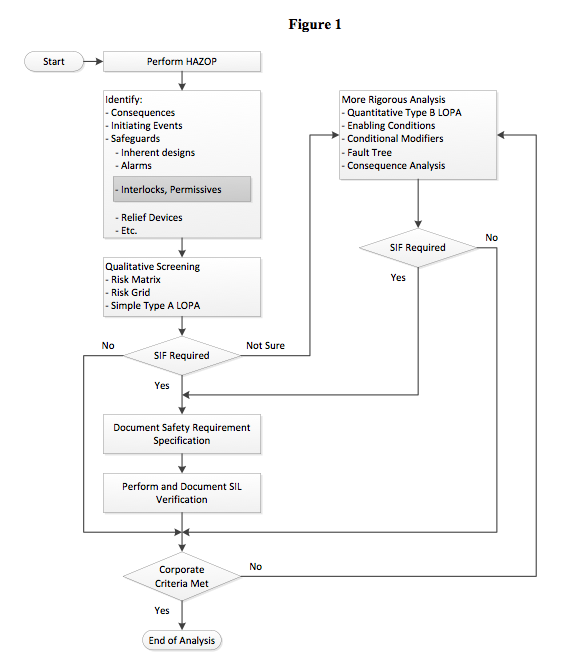
In some cases the screening methods will indicate that a SIF is needed. These screening methods can be designed to determine how many orders of magnitude risk reduction is needed, allowing a required SIL to be documented for a particular SIF. The screening…
Read More...
- by Hal Thomas, CFSE
- Friday, June 29, 2012
- Functional Safety
Relating Test Data to Operating Modes & “Proven in Use”
Everyone wants data, and generally everyone agrees high quality proven in use data is the best. Properly designed experimental testing is one means to simulate actual operation. That is what we all learned as far back as high school during our chemistry and physics labs. These tests can…
Read More...
- by Hal Thomas, CFSE
- Tuesday, May 24, 2011
- Functional Safety
When is a Variable Frequency Drive a SIS?
It used to be that a pump would operate at a single speed dictated by a motor, thus fixing the pump curve. As the discharge flow decreased due to a restriction downstream, the pump outlet pressure would increase reaching its deadhead pressure. If the downstream piping and vessels were…
Read More...


